Processes
You might run an email program and a web browser, both client applications, on your PC at the same time, and your email and web server might both run on the same server. Even so, emails end up in your email application and web pages end up in your web browser.
Port Numbers
A port is a 16-bit number that's used to direct traffic to specific services running on a networked computer.

Socket Address

IP + Port = Socket Address
Multiplexing and Demultiplexing
- Multiplexing in the transport layer means that nodes on the network have the ability to direct traffic toward many different receiving services.
Demultiplexing is the same concept, just at the receiving end, it's taking traffic that's all aimed at the same node and delivering it to the proper receiving service.

Headers & Payload
At every layer, the data packets consist
- Header
Header of data link layer frame contains MAC address
Header of Network layer datagram contains IP address
- Header of Transport layer Segment contains Port number
- Payload
Protocols
Protocols used in transport layer:
Transmission Control Protocol (TCP)
User Datagram Protocol (UDP)
Packets
At each layer, a larger message is broken down to smaller messages.
Sending smaller messages is more efficient than sending a large message over a network.
The sending end system breaks the data into smaller parts known as packets

Route
ANALOGY: Transportation Network
Buildings, Roads, Highways, Intersections, Trucks ..
The sequence of communication links and packet switches traversed by a packet from the sending end system to the receiving end system is known as a route or path
The routers are constantly trying to balance the load across whataevere routes they know to ensure speedy and reliable delivery which is conjunction control

Sequence Numbers
TCP ensure the packets reassembled in right order.
A 32-bit sequence number is used to keep track of the order of segments.

Packet Loss
Data Packets can be lost in transit over the network.
TTL Expired
Network Congestion
Network Hardware Failures
Transmission Control Protocol
TCP provides mechanisms to ensure that data is reliably delivered.
Acknowledgement
TCP protocol ensure reliable data transfer by sending acknowledgement for each message received
The acknowledgment includes the sequence number of the next expected segment.
TCP Connection
SYN (Synchronize): Used to initiate and establish a connection. It also helps you to synchronize sequence numbers between devices.
FIN (Finish): Used to terminate a connection when the transmitting computer doesn't have any more data to send.
Establishing TCP Connection: Three - Way HandShake
A handshake is a way for two devices to ensure that they're speaking the same protocol and will be able to understand each other.
After completion of three-way handshake actual data transfer starts.

Data Transmission
Operation With No Loss
- Once the three-way handshake is complete, the application data can begin to flow between the client and the server.
- The client can send a data packet immediately after the ACK packet
- When a packet of data is sent over TCP, the recipient must always acknowledge what they received.
- The first computer sends a packet with data and a sequence number.
- The second computer acknowledges it by setting the ACK bit and increasing the acknowledgement number by the length of the received data.
Those two numbers help the computers to keep track of which data was successfully received, which data was lost, and which data was accidentally sent twice.

Lost Packet
- TCP connections can detect lost packets using a timeout.
- After sending off a packet, the sender starts a timer and puts the packet in a retransmission queue.
- If the timer runs out and the sender has not yet received an ACK from the recipient, it sends the packet again.

Lost ACK

Premature timeout
- The retransmission may lead to the recipient receiving duplicate packets, if a packet was not actually lost but just very slow to arrive or be acknowledged.
- If so, AS recipient has sequence it can simply discard duplicate packets.
It's better to have the data twice than not at all!

Terminating TCP Connection: Four - Way Handshake
To Close the Connection four way handshake happens

Internet traffic
TCP - Congestion Avoidance
Two phases in TCP Congestion Control Algorithms
Slow Start
Congestion Avoidance
Slow Start Phase: When connection begins increases rate exponentially(1, 2, 4, 8, 16…) until first packet loss. due to overload or congestion that packets may be dropped. Packets lost will trigger a timeout at the sender. When this happens, the sender goes into congestion avoidance phase
Example : first 1 packet is sent and got 1 ack , next doubles 2 packets is sent and after successful two acks it now send four packets the process goes on until the packet got lost.
Congestion Avoidance Phase: In the Congestion Avoidance. It increase rate linearly. If congestion was indicated by a timeout, the congestion window is reset to one segment, which automatically puts the sender into Slow Start mode.
Example: the packet was lost at 4 segments in slow start so, in congestion avoidance phase it send again 4 segments after successful acks it increment by one and so the next it sends 5 segments . if the packet was lost. It reset with one segment it automatically puts the sender into Slow Start mode.

Transmission Control Protocol
Establish the connection
Send constant stream of acknowledgments
Tear the connection down at the end
TCP vs UDP

Let's imagine that each UDP datagram is a single frame of a video. For the best viewing experience, you might hope that every single frame makes it to the viewer, but it doesn't really matter if a few get lost along the way. A video will still be pretty watchable unless it's missing a lot of its frames.
So, in Most video chats like skype and game streaming, video and music streaming, etc. uses UDP. That’s if you are on bad internet connection skype get all gitchy. Not all UDP packets are delivered to your system.
But this approach doesn’t work for other application like it doesn't really work if you send an email and shows up with the middle part missing. The whole message really needs to get there correctly.when it absolutely, correctly needs to get there programs uses TCP ( Transmission Control Protocol)
User Datagram Protocol
Referred to as a "null protocol",
Provides no guarantees about message delivery or notifications of failure
Less Overhead
IP Addresses
Public & Private IPs
Internet Assigned Numbers Authority (IANA) assigns different IP ranges to different organizations and Internet Service Providers
Certain range of IPs are reserved for Private Usage
| Private IP Address Ranges | Possible Hosts |
|---|---|
| 10.0.0.0 to 10.255.255.255 | 16777216 |
| 172.16.0.0 to 172.31.255.255 | 1048576 |
| 192.168.0.0 to 192.168.255.255 | 65536 |
Network Layer
Non-Routable Address Space
- RFC(Request for Comments) 1918 defined non-routable address space.
- Non-routable address space are ranges of IPs set aside for use by anyone that are not registered in the internet.
- RFC 1918 defined three ranges of IP addresses that will never be registered in the internet anywhere are 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16.
This IP address are used only internally like home network or business

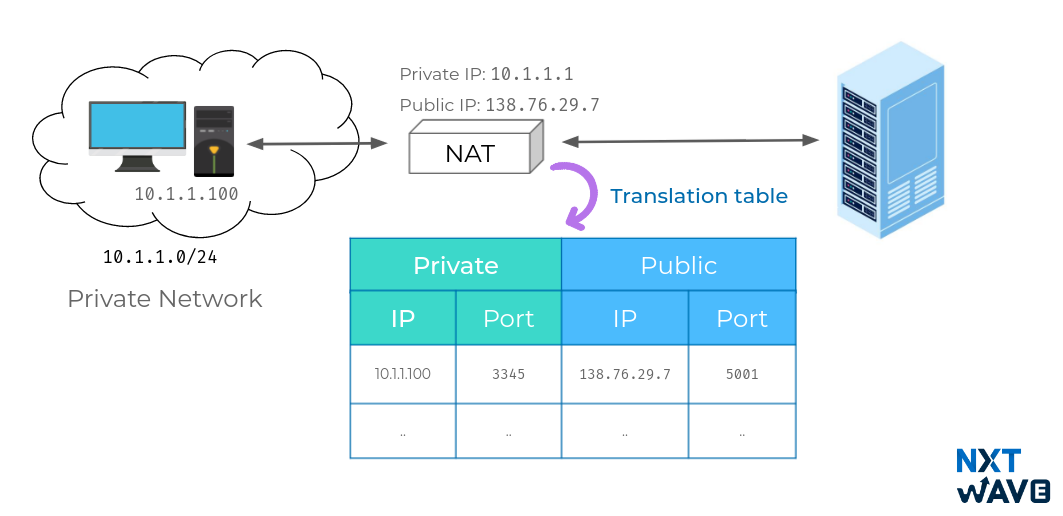
Network Address Translator
- With NAT, you can have hundreds even thousands of machines using non-routable address space.
- Yet, with just a single public IP, all those computers can still send traffic to and receive traffic from the internet.
- All you need is one single IPv4 address and via NAT, a router with that IP can represent lots and lots of computers behind it.

NAT is a technology that allows a gateway, usually a router, to rewrite the source IP of an outgoing IP datagram while retaining the original IP in order to rewrite it into the response.
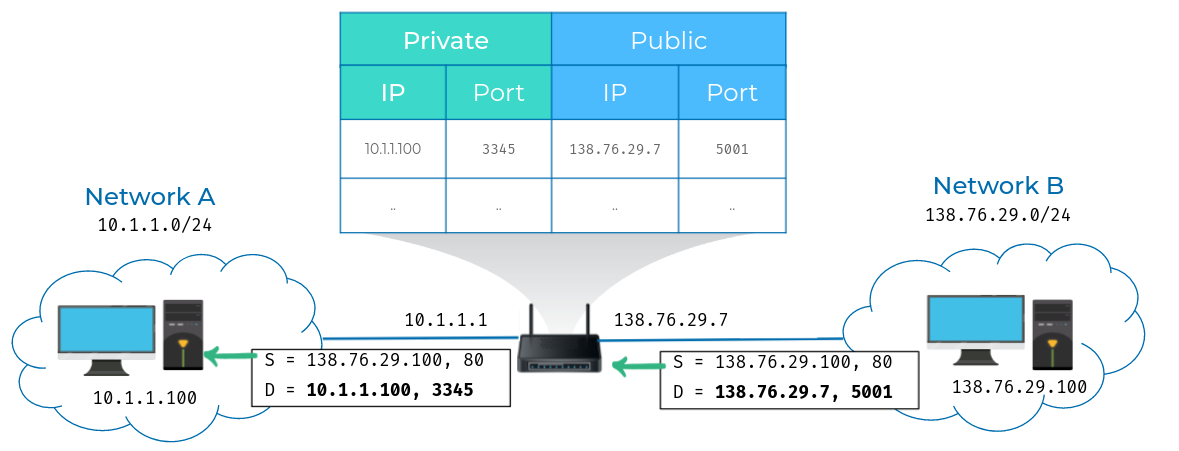
- Here, we have two networks. Network A consists of the 10.1.1.0/24 address space and network B consists of the 138.76.29.0/24 address space. Sitting between these networks is a router that has an interface on network A with an IP of 10.1.1.1 and an interface on network B of 138.76.29.7. Computer 1 is on network A and has an IP of 10.1.1.100. And computer 2 is on network B and has an IP of 138.76.29.100.
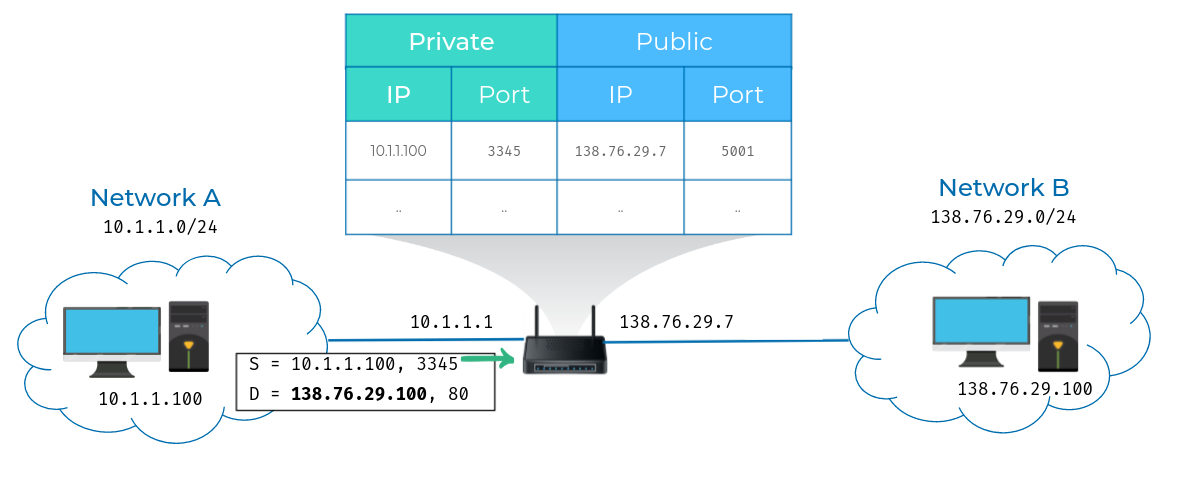
- Computer 1 wants to communicate with a web server on computer 2.
- So it crafts the appropriate packet at all layers and sends this to its primary gateway, the router sitting between the two networks.
- So far, this is a lot like many of our earlier examples, but in this instance,
- The router is configured to perform NAT for any outbound packets.
- Normally, a router will inspect the contents of an IP datagram, decrement the TTL by 1, and forward the rest of the data at the network layer without touching it.
But with NAT, the router will also rewrite the source IP address, which in this instance, becomes the router's IP on network B or 138.76.29.7. When the datagram gets to computer 2, it'll look like it originated from the router, not from computer 1.
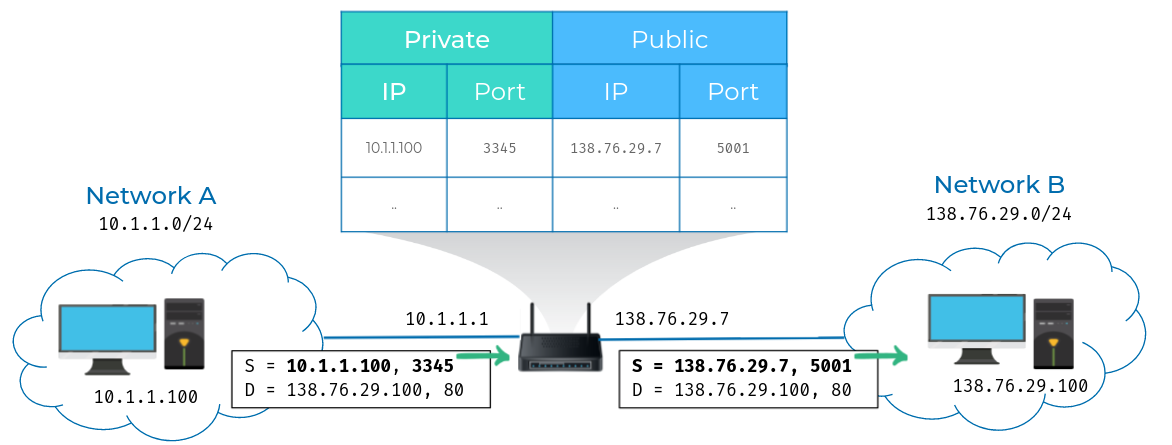
Now, computer 2 crafts its response and sends it back to the router. The router, knowing that this traffic is actually intended for computer 1, rewrites the destination IP field before forwarding it along.